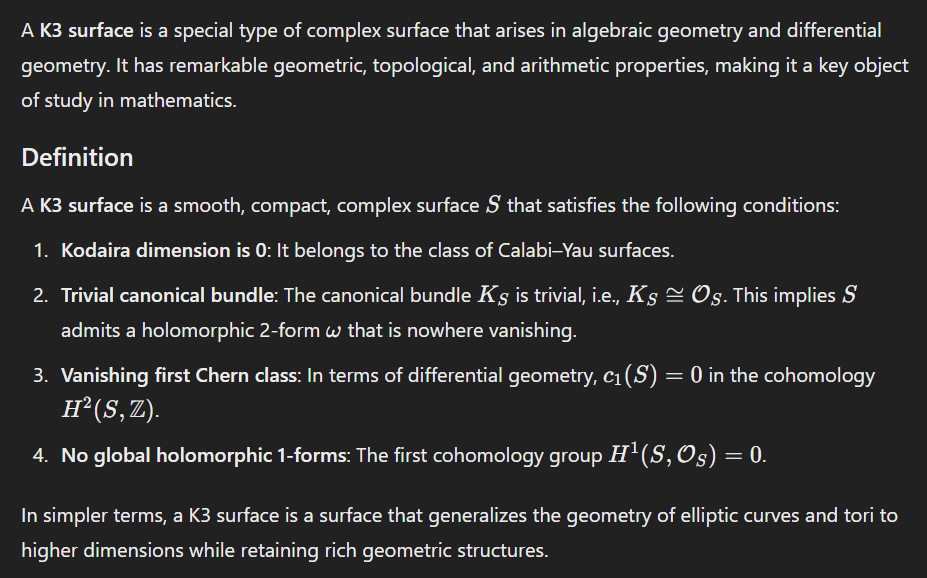
版主: verdelite, TheMatrix




这篇介绍的不错。这也是ChatGPT的回答吧?FoxMe 写了: 2024年 11月 20日 12:35 K3 surface是椭圆曲线的推广,可能在密码学中有用。可能比椭圆曲线密码强吗?
K3 surfaces and elliptic curves both have significant roles in algebraic geometry and number theory, but their potential applications in cryptography differ substantially due to the mathematical structures they provide. Let’s analyze whether K3 surfaces could replace or "beat" elliptic curves in cryptographic applications.
1. Cryptographic Advantages of Elliptic Curves
Elliptic curves are widely used in cryptography (e.g., Elliptic Curve Cryptography, or ECC) because:
Group Structure: The set of rational points on an elliptic curve forms an abelian group, which is crucial for cryptographic operations.
Hard Problems: Problems like the Elliptic Curve Discrete Logarithm Problem (ECDLP) are computationally hard, providing security for cryptographic schemes.
Efficiency: The group law for elliptic curves is efficient to compute, making elliptic curve-based cryptography lightweight and suitable for constrained devices (e.g., IoT).
These features make elliptic curves ideal for public-key cryptography.
2. K3 Surfaces: A General Overview
K3 surfaces are two-dimensional algebraic varieties with rich geometric and arithmetic structures. They satisfy:
)≅C, which implies they are compact and have trivial canonical bundles.
They generalize elliptic curves in some sense because they can sometimes admit elliptic fibrations, meaning they are equipped with maps to a curve where the fibers are elliptic curves.
However, K3 surfaces are not equipped with a natural group structure in the way elliptic curves are. While there are constructions involving elliptic fibrations, these fibrations rely on the elliptic curves themselves.
3. Potential Use of K3 Surfaces in Cryptography
There have been studies on the use of higher-dimensional varieties in cryptography, including K3 surfaces, for problems related to lattice-based cryptography or higher-dimensional abelian varieties. However, there are significant challenges:
(a) Lack of Group Structure
Cryptographic protocols based on elliptic curves (e.g., ECDSA, ECDH) rely fundamentally on the group structure of elliptic curves. K3 surfaces, as they stand, lack a natural group law, making them less suitable for such protocols.
(b) Complexity
The arithmetic and geometry of K3 surfaces are much more complex than elliptic curves:
Operations on K3 surfaces would involve significantly higher computational overhead.
The lack of efficient algorithms for explicit arithmetic operations makes them impractical compared to elliptic curves.
(c) Hard Problems
K3 surfaces might offer hard computational problems for cryptography, such as:
Problems related to their cohomology groups.
Understanding rational points or sections of their elliptic fibrations. However, such problems are not as well-studied or established in cryptography as the discrete logarithm problem for elliptic curves.
4. Post-Quantum Cryptography
In the context of post-quantum cryptography, cryptosystems must resist attacks from quantum computers:
Elliptic curve-based cryptography (like ECC) is vulnerable to Shor's algorithm, which efficiently solves the discrete logarithm problem on a quantum computer.
K3 surfaces might offer resistance to quantum attacks if certain problems tied to their geometry (e.g., cohomological problems or torsion points on elliptic fibrations) are proven to be quantum-hard. However, this is speculative and lacks the extensive research base of alternatives like lattice-based, hash-based, or code-based cryptosystems.
5. Comparison: Elliptic Curves vs. K3 Surfaces
Feature Elliptic Curves K3 Surfaces
Group Structure Yes (abelian group) No (except fibrations via elliptic curves)
Efficiency of Operations Highly efficient Computationally expensive
Hard Problems Well-studied (ECDLP) Less studied and less established
Cryptographic Usage Widely deployed (ECC) Experimental or speculative
Post-Quantum Potential Vulnerable to quantum attacks Possible resistance, but speculative
6. Conclusion
While K3 surfaces are fascinating from a mathematical perspective, they are unlikely to "beat" elliptic curves in cryptography, at least for now. The lack of a natural group structure, computational inefficiency, and limited research into cryptographic applications make them unsuitable for most current protocols.
However, K3 surfaces (or higher-dimensional varieties in general) could play a role in developing new cryptographic primitives, especially in post-quantum cryptography, if hard problems tied to their geometry prove to be resistant to quantum and classical attacks. For now, elliptic curves remain the practical and dominant choice.
